Knifefish Submersible Drone Hunts for Hidden Mines
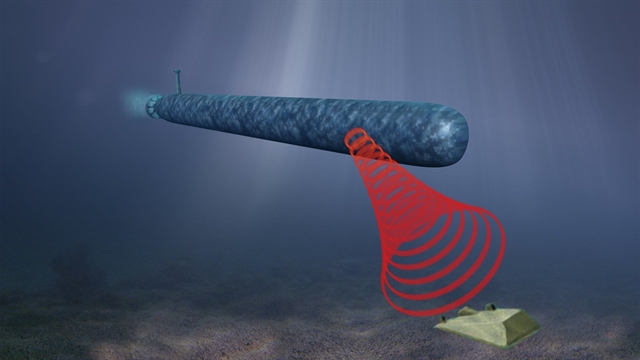
The General Dynamics Mission Systems (GDMS) team responsible for the development of the Knifefish autonomous submersible has announced that the drone has, in coordination with the U.S. Navy, successfully completed a mine-hunting evaluation off the coast of Boston.
The evaluation used Navy mine test targets and represents an important milestone in the Knifefish program. The purpose of the test was to demonstrate the Knifefish’s capabilities in action and gather data that will help to refine future iterations of the drone.
The Knifefish is a heavyweight-class mine countermeasure (MCM) unmanned undersea vehicle (UUV) intended for deployment from Navy surface vessels. The UUV is designed to detect and classify a wide range of potential mines situated at varying depths in the ocean, as each type of mine presents unique dangers to naval ships. The Knifefish can also identify mines buried in the seafloor.
Home Designing in a 3D Environment
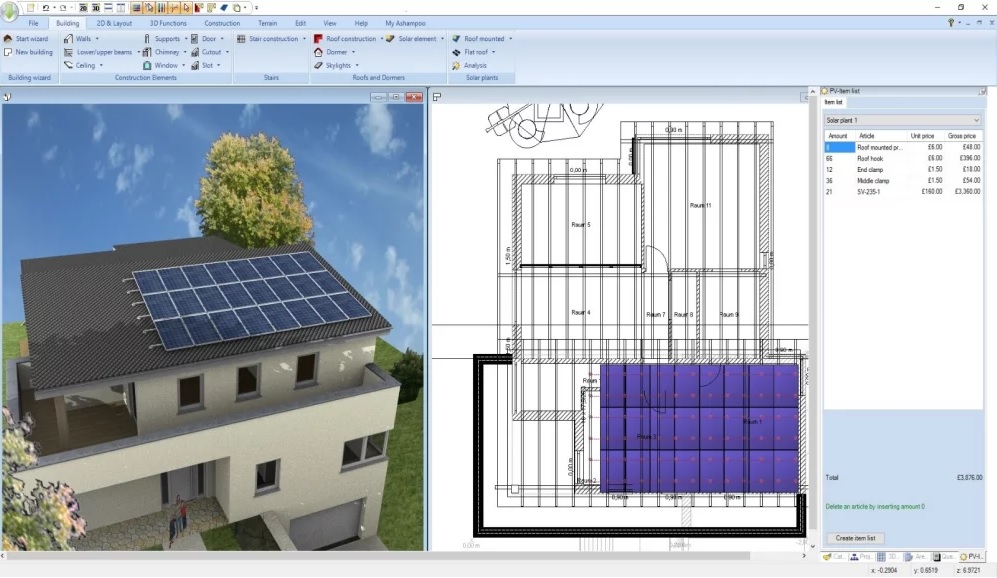
Software development company Ashampoo has released the fourth installation of its Home Designer Pro series, Home Designer Pro 4, a computer-aided design (CAD) program that enables users to plan, build and preview virtual structures in a 3D environment. The number of digital domiciles that users can create with the software is almost unlimited, ranging from tiny shacks to enormous mansions.
Aside from featuring millions of ready-to-use objects that users can select to furnish their dwellings, Home Designer Pro 4 supports the loading, editing and saving of various 3D object formats. In addition, Google SketchUp and COLLADA models are compatible with Ashampoo’s software and can be imported with ease.
Ashampoo has attempted to make Home Designer Pro 4 as intuitive as possible. The program uses a ribbon toolbar that groups all functions logically and thematically, and also automatically performs mathematical calculations related to the angle, length, area or volume of a structure. This feature saves time and lets users skip the math needed for such calculations in order to focus solely on their designs.
Fantastic Voyage—Flying Through a Turbine Blade

Researchers from Oak Ridge National Laboratory (ORNL)’s Spallation Neutron Source (SNS) have recently utilized neutron imaging to examine the cooling channels and other inner workings of Inconel 718 turbine blades. The blades were created using additive manufacturing, and the neutron imaging provides a way to nondestructively study the internal structure of the blades in order to improve their design.
Turbine blades are complicated and delicate pieces of engineering. Each blade has cooling channels that allow air to flow through and exit the porous shell of the blade, maintaining a stable temperature for the assembly. Due to their nature, each turbine blade requires a series of rigorous testing procedures in order to verify their structural integrity.
Visually observing the exterior casing of the blades is a simple matter, but capturing images of their internal structure (without physically cutting the turbine blades open) is no easy task. Bernie Riemer, senior research engineer at ORNL, gave a presentation about this topic on the last day of Dassault Systèmes’ Science in the Age of Experience in Chicago. Riemer explained that building a neutron imager is difficult and that the imager at ORNL functions by moving mercury at speeds that are high enough to cause cavitation.
New Study Shines Light on Darknet’s Digital Defenses

Researchers have often questioned how the Darknet—the part of the Internet only accessible via specific software—is able to ward off the vast majority of the digital attacks directed against it. Now, new avenues of inquiry regarding the strength of the Darknet’s defenses have been opened by Manlio De Domenico and Alex Arenas from the Universitat Rovira i Virgili (URV)’s Department of Computer Engineering and Mathematics.
In a recent study, Arenas and De Domenico utilized network analysis and new data stemming from UCLA’s Internet Research Lab to construct a topological model of the Darknet, demonstrating how information is transmitted through the use of “onion routers,” which encrypt messages in multiple layers. The model has revealed that the unique topology and structure of the Darknet renders it almost impenetrable to attacks.
For many years, the Darknet has been the subject of controversy, intrigue and mystery. Rumors have long abounded concerning the secretive and often illicit exchanges that occur anonymously and away from the prying eyes of the authorities. This new appraisal of the Darknet’s robust nature may shed some much-needed light into the shadowy crevices of the infamous network.